Friday 4 October 2013
AVG 2013 Crack Valid until 2017 Free Download
Download Cracked Internet download Manager 6.12 Final Version 2013

Download Cracked Internet download Manager 6.12 Final Version 2013
Internet download Manager (IDM) could be a tool to extend download speeds by up to five times, resume nd chedule downloads. Comprehensive error recovery and resume capability can restart broken or interrupted downloads because of lost connections, network issues, laptop shutdowns, or surprising power outages. easy graphic-computer program makes IDM user friendly and straightforward to use.Cracked Internet download Manager 6.12 Final Version encompasses a good transfer logic accelerator that options intelligent dynamic file segmentation and safe multiplier downloading technology to accelerate your downloads.
cracked internet download manager supports proxy servers, ftp and HTTP protocols, firewalls, redirects, cookies, authorization, MP3 audio and MPEG video content process. IDM integrates seamlessly into Microsoft net individual,Netscape, MSN individual, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Firebird, Avant Browser, MyIE2, and every one alternative well-liked browsers to mechanically handle your downloads.
Download Cracked Internet download Manager 6.12 Final Version 2013
File Information
File: IDM 6.12 Build 26 with Crack.zip
Size: 6.09 MB
Size: 6.09 MB
***Instruction***
- Install idman612.exe
- Close Internet Download Manager in Tray Icon.
- Copy "IDM an" in Crack Folder and Paste into "C:\Program Files\Internet Download Manager"
Mcafee security Plus Lifetime Crack Serials 2013
Mcafee security Plus Lifetime Crack Serials 2013
MacAfee internet Security 10 Established security that shield against viruses and spyware.Protect distinctive files, like folks photos and private monetary documents.
Identify spyware,threats and adware before they will run on your laptop.
Cleans viruses and virus-like concern automatically.
Prevent the stretch of viruses to alternative pcs.
Updates automatically to shield against new threats.
How to use Mcafee security Plus Lifetime Crack Serials 2013
Use Blow Promo Code For Mcafee Registration.
VSPPROMOCF
MacAfee Free Activation Key Free 2013 area unit Blow
License Key: 03GK-S3KR-7FUUH-6J26-0G0N
Mcafee v5.20: E000-VB14-G8RY
McAfee VirusScan v4.5.0.534: E000-VB14-G8RY
Download Required File through Downloader (Fast Instalation)
Sys Information
Sys Information is a free program (also open source) to see more detailed information or specifications of the computer (windows) are used. 1000% Free Software Downloads
Source: http://arvinsoft.weebly.com/sys-information.html
Jelly Bean, Android Most Secure
Android 4.1 or better known as Jelly Bean claimed to be more secure and harder than any other version hacked. Because this is the first version of Android that meets the Address Space Layout Randomisation (ASLR).
ASLR itself is a standard security against hackers who are looking for ways to install malware on the user's device.
ASLR randomizing the memory locations for the library and other data structures, making it difficult for cyber criminals to smuggle malware (malicious programs) on the handset. This report is based on the results of the study a number of hackers and security firms on security arrangements in the Jelly Bean.
"As long as something is not random and ASLR does not work as long as the hacker knew it was there at the same location, they can use it to break into anything," said Charlie Miller, a security researcher from research firm Accuvant.
Miller pointed out, Jelly Bean is the safest current Android and Android first to have full ASLR.
ASLR itself is a standard security against hackers who are looking for ways to install malware on the user's device.
ASLR randomizing the memory locations for the library and other data structures, making it difficult for cyber criminals to smuggle malware (malicious programs) on the handset. This report is based on the results of the study a number of hackers and security firms on security arrangements in the Jelly Bean.
"As long as something is not random and ASLR does not work as long as the hacker knew it was there at the same location, they can use it to break into anything," said Charlie Miller, a security researcher from research firm Accuvant.
Miller pointed out, Jelly Bean is the safest current Android and Android first to have full ASLR.
New capabilities of Microsoft Office
All-Touch: Office responds naturally touches such as the keyboard and mouse. Use your finger to replace the screen or zoom in and out the size of the document. Create new content and access cool features, just with the touch of a finger.
-. Digital Writing: Use the stylus to create content, record and access our other features. Reply to email with handwriting and automatically converted into text. Use your stylus as a laser pointer during a presentation. Paint your content and easily remove mistakes.
-. New applications Windows 8: OneNote and Lync represents a new generation of Office applications that use the Windows 8. Both applications are designed to give priority to the touch interface on a tablet. A new radial menu in OneNote makes it easy to access all the features of a finger.
-. Included in the Windows RT (WinRT): Office Home & Student 2013 RT, which include the latest versions of Word, Excel, PowerPoint and OneNote, will be included in Windows 8 ARM-based devices, including Microsoft Surface.
. SkyDrive: SkyDrive Office to save documents by default, so that your documents are always available throughout the tablet, PC and mobile phones. The document is also available online and will be synchronized when reconnected to the internet.
-. Roaming: After Sign In, personal settings will be automatically available in almost all devices, including most recently used files, templates and even a dictionary that you normally use. Office even remember your last position and bring you back into position with one click.
-. Office on Demand: The Office subscription, you can use Office from any computer - Windows-based computer that is connected to the internet.
-. Subscription service: The new Office is also available as a cloud-based subscription service. As a customer, consumer automatically gets the latest version of the upgrade in addition to other cloud services world interest include Skype minutes and additional storage capacity of SkyDrive. Subscribers also have the right to install in a variety of devices that belong to a family member.
-. Yammer: Yammer is claimed as a safe social networking for business. You can register for free and immediate use. Yammer also integrates with SharePoint and Microsoft Dynamics.
-. Always Connected: Connect with anyone (whether a friend or a work team), and documents through SharePoint sites. View and include pictures, video and content around current activity so that all your friends and colleagues can always be updated.
-. People Card: Office integrates all your contacts. Card People include presence information, is equipped with the latest status, contact information and events from Facebook and LinkedIn accounts.
-. Skype: Skype is equipped with the latest Office. When you subscribe, you get 60 minutes of world Skype minutes per month. Integrate Skype into Lync all contacts, so you can call and send instant messages to anyone on Skype.
-. Recorded digitally: Use OneNote to store all your notes in the cloud and in the range of your device. Use the notes that you like - touch, digital pen, keyboard, or a combination of everything.
-. Read and mark: Read Mode in Word provides a modern reading experience and easily, which automatically adjusts the size of the screen, both big and small. Zoom in and out of content, the video stream in the document, see the revision marks and back pages with the touch.
-. Meeting: PowerPoint to introduce the new Presenter View, which in one screen displays the currently displayed slide, next slide, the presentation period, and notes for the speaker.
-. When doing a presentation, you can zoom, mark, and the slide control with touch and stylus. Lync provides a multi-party HD video presentations, share your OneNote notes and virtual whiteboard for discussion.
Offers complete price list and will be announced in the fall of the United States this year. However, Steve Ballmer describes three services subscribed to the new Office 365.
When available, each new subscription offerings will include the Office applications 2013 edition - Word, Excel, PowerPoint, OneNote, Outlook, Publisher and Access.
In addition, every customer has the right to get an upgrade to the latest version in the future, as well as the right to use up to five PCs or Macs and mobile devices.
The third edition is the latest:
-. Office 365 Home Premium - is designed for family and consumer. This service also includes an additional 20 GB of storage on SkyDrive and 60 minute world Skype minutes per month.
-. 365 Small Business Office Premium - designed for small businesses. These services also include email, shared calendars, website tools and web conferencing business-class HD.
-. Office ProPlus 365 - designed for large enterprise customers who want to have a high level bisni ability and flexibility to deploy and manage in the 'cloud'.
-. Digital Writing: Use the stylus to create content, record and access our other features. Reply to email with handwriting and automatically converted into text. Use your stylus as a laser pointer during a presentation. Paint your content and easily remove mistakes.
-. New applications Windows 8: OneNote and Lync represents a new generation of Office applications that use the Windows 8. Both applications are designed to give priority to the touch interface on a tablet. A new radial menu in OneNote makes it easy to access all the features of a finger.
-. Included in the Windows RT (WinRT): Office Home & Student 2013 RT, which include the latest versions of Word, Excel, PowerPoint and OneNote, will be included in Windows 8 ARM-based devices, including Microsoft Surface.
. SkyDrive: SkyDrive Office to save documents by default, so that your documents are always available throughout the tablet, PC and mobile phones. The document is also available online and will be synchronized when reconnected to the internet.
-. Roaming: After Sign In, personal settings will be automatically available in almost all devices, including most recently used files, templates and even a dictionary that you normally use. Office even remember your last position and bring you back into position with one click.
-. Office on Demand: The Office subscription, you can use Office from any computer - Windows-based computer that is connected to the internet.
-. Subscription service: The new Office is also available as a cloud-based subscription service. As a customer, consumer automatically gets the latest version of the upgrade in addition to other cloud services world interest include Skype minutes and additional storage capacity of SkyDrive. Subscribers also have the right to install in a variety of devices that belong to a family member.
-. Yammer: Yammer is claimed as a safe social networking for business. You can register for free and immediate use. Yammer also integrates with SharePoint and Microsoft Dynamics.
-. Always Connected: Connect with anyone (whether a friend or a work team), and documents through SharePoint sites. View and include pictures, video and content around current activity so that all your friends and colleagues can always be updated.
-. People Card: Office integrates all your contacts. Card People include presence information, is equipped with the latest status, contact information and events from Facebook and LinkedIn accounts.
-. Skype: Skype is equipped with the latest Office. When you subscribe, you get 60 minutes of world Skype minutes per month. Integrate Skype into Lync all contacts, so you can call and send instant messages to anyone on Skype.
-. Recorded digitally: Use OneNote to store all your notes in the cloud and in the range of your device. Use the notes that you like - touch, digital pen, keyboard, or a combination of everything.
-. Read and mark: Read Mode in Word provides a modern reading experience and easily, which automatically adjusts the size of the screen, both big and small. Zoom in and out of content, the video stream in the document, see the revision marks and back pages with the touch.
-. Meeting: PowerPoint to introduce the new Presenter View, which in one screen displays the currently displayed slide, next slide, the presentation period, and notes for the speaker.
-. When doing a presentation, you can zoom, mark, and the slide control with touch and stylus. Lync provides a multi-party HD video presentations, share your OneNote notes and virtual whiteboard for discussion.
Offers complete price list and will be announced in the fall of the United States this year. However, Steve Ballmer describes three services subscribed to the new Office 365.
When available, each new subscription offerings will include the Office applications 2013 edition - Word, Excel, PowerPoint, OneNote, Outlook, Publisher and Access.
In addition, every customer has the right to get an upgrade to the latest version in the future, as well as the right to use up to five PCs or Macs and mobile devices.
The third edition is the latest:
-. Office 365 Home Premium - is designed for family and consumer. This service also includes an additional 20 GB of storage on SkyDrive and 60 minute world Skype minutes per month.
-. 365 Small Business Office Premium - designed for small businesses. These services also include email, shared calendars, website tools and web conferencing business-class HD.
-. Office ProPlus 365 - designed for large enterprise customers who want to have a high level bisni ability and flexibility to deploy and manage in the 'cloud'.
Apple Success Story: Beginning Have No Money
"When I initiated Apple with Steve Jobs, we had no money at all. We just had an idea and a strong motivation. Motivation is what lies within us, more valuable than money," said Woz, greeting familiar, while sharing the story success of Apple in Balai Kartini, Jakarta.
The idea and motivation that was poured in the form of creative product innovation that is useful for many people, and have more added value so that people are willing to spend money to buy it.
"Apple has listed the history, building a computer that is easy to use, intuitive, without the need to learn to use it. People are more important than technology. You have to hide the microprocessor so as not to look. Get rid of anything that prevents a normal life."
Armed with the skills they mastered while working for another company - Wozniak at Hewlett-Packard and Jobs at Atari - they both agreed founded Apple in 1976. "Let us make the company," recalls Wozniak Steve Jobs imitation invitation to him at that time.
"Before the start of Apple, Steve Jobs and I had been friends for over five years. We split the money-fifthy fifthy. He was working for Atari, and he found a way to sell. We started the partnership. We started from the garage, where we live."
Wozniak whiz in technical matters, and Jobs is okay in the recognition of marketing a product. "There are people who are not expert in the field of technology, but these people have big dreams. Meanwhile, I always wanted was a super programmer. People are usually reluctant to conflict with the technology to others."
Who would have thought, they pioneered the company from a garage 36 years ago, has now become one of the world's leading technology companies. Mac computers, iPod music players, cell phones iPhone and iPad tablet, is an example of the success of Apple products.
"Do not hijack someone else's idea. I do not have money, then I have to think hard. I kept asking myself, what people need. I have to create something that has not been made by others. Soon get the answer, we were slow-slow step. Do one at best, "said Woz.
Dreams Become Engineers
Woz admitted lucky to have parents who understood him. His father was a bloody Poland, also an engineer like him. "I am very interested in science fiction. I knew I would become an engineer at the age of 10 years," recalls Woz is known as a veteran engineer of the Sillicon Valley.
"I am a small person of shy, afraid to talk to other people. Not had a boyfriend at the time, so I had plenty of time to ponder each home. My head filled with ideas," said the man who designed the online hotel booking for the first time then.
Good ideas often found them in unexpected moments. "I lie awake at night. Reading emails and sometimes tamper with the computer. Between waking and sleeping I often think about technology products. I never used drugs. I also do not think the ideas are always coming in at odd moments, "he said.
Wozniak went back to commemorate the forerunner of which he founded Apple with Steve Jobs. They both did meet in a bevy of computer clubs whose members include technology geeks where one of them is Bill Gates, founder of Microsoft.
"When Bill Gates came with the computer language BASIC, I never tried it. But then I learned at Hewlett-Packard and Apple to create an embryo. Then Steve Jobs came up to me. 'Oh my God, let us make the company'. So I (Apple employee ) number one and number two Steve Jobs, "recalls Wozniak.
Although it has been very successful, Woz claimed never shut down. He was always passionate about every talked about technology and always open to anyone. He claimed to always read the incoming email and even phone calls he had never delegated to his secretary.
"My philosophy is what makes life so simple. People will tend to hide the big questions, and answers, the truth is the culmination of all goodness. Truth for me is to tell everyone about me, what I do. Internet has brought us to this level. I have no fear of openness. "
Spirit of openness also makes love to the open source programming. "Open source is controlled young people, like my first. With open source, we can see the contents of the program. We can get ideas by seeing what other people did. We could start with things that are simple and economical. That usually innovation that began, "said Woz.
Jobs Try Firing CEO
Apple's huge success in the market today, also had experienced ups and downs. He came out of Apple and Steve Jobs was forced to leave the company. He said it was normal in a profit-oriented business organizations. But the return of Steve Jobs, the company was again shot up to date.
"I do not get bored with Apple at the time. I left Apple because I had the idea to build a universal remote control. I also developed a chip as a replacement hard drive with solid state disc. I love developing new items. I also had amnesia after a plane crash . Then, I also go back to college at UC Berkeley to catch up, "Woz reveals the reason.
"While Jobs, he has a bad reputation at a certain point. He was dismissed from his role after trying to dismiss our CEO. He was dismissed from his authority, but not out of Apple. He felt constrained to do the things he loves. Trying to build a great computer for world. Apple products actually defines the work Steve. Almost all Apple products are a representation of Steve Jobs, "he continued.
"Now that Steve Jobs has left us. How I miss him very much. I hope he is here, accompanied me to share knowledge and passion about technology. I do not think there is a technology leader like him," recalls Woz with teary eyes.
Provision of a valuable life experience, Wozniak did not forget to instruct the young children in Indonesia.
"Pursue your dreams to the skies. Not buried thoughts and do not let your ideas slip by. It's OK to work in the company of people to generate income, but do not waste your youth. You have to start writing a 'book' of your own and come up with a plan for your own life. Do not be afraid to think for yourself. Do not be afraid that your ideas are not as good as other people, "Woz closed.
Vertex, Tablet 'Four Brains' Successor of HTC Flyer
McAfee Anti-virus Plus 2012-2013 6 months trial

McAfee Anti-virus Plus 2012-2013 6 months trial
McAfee is presently giving one all told their best product with a six month bonus without charge.
The system desires consists of running:
Windows Xp with SP3
Windows prospect
Windows seven,also you would like a
Minimum of 512MB Ram and a
The major advantage of this product area unit the:
Antivirus Protection – this complete feature protects you against net threats like trojans,malwares and spywares but owing to the McAfee Active protection all the suspicious files area unit analyzed even before being downloaded to your computer.Also all the removable devices along side USB’s,are scanned to seek out even the best crafted malware.
Firewall – the two day firewall is improbably effective in interference potential harmful web traffic or applications,that want to connect to net.Also when you would like to travel looking on-line the safe website} area unit marked with inexperienced supported SSL certificates and their trustworthy belongings you acknowledge if you run throughout a phishing website,a scamming internet site or a legit one.
Email protection – If you are exploitation Outlook then McAfee will scan the emails for your and permit you to acknowledge if one factor is strange.
Beside those blessings McAfee throws a handful of bonus {the computer|the computer} Tune-up that helps your pc to reinforce the booting speed and additionally the digital data device.
Now if you wish to do for a full six months.
macafer antivirus key serial 2012-13,mcafee v8 update,download macfee key serial updates,mcafee security tired one free key serial 2012-2013,mcafee info update 2012-13,internetsecurity 2012-13 Key Serial Updates Latest,free transfer mcafee enterprise 9 full
To Download McAfee Anti-virus Plus 2012-2013 6 months trial Click Here
Follow the steps:
- Go to Promo Page and click “Get Started Now”
- Create a new account, filling the spaces.
- Check your email for activation link.
- Click download button,accept the ToS and then click again the download button.
We square measure sharing some McAfee Key Serial Updates Free 2012-2013
Update and Register your mcafee antivirus exploitation blow provided License key serials.
If anyone key not work comment blow for additional data..............
License Key: 03GK-S3KR-7FUUH-6J26-0G0N
License Key: 1CHD-23CR-K493R-UGM6-0G1F
S/N: 193746
Download Required File through Downloader (Fast Instalation)
Thursday 3 October 2013
How to Install Windows 7 on VirtualBox
Following on from our article about running Windows 7 within Microsoft Virtual PC, this tutorial will show you how to run Windows 7 by using the more powerful VirtualBox application.

VirtualBox is an open-source tool from which you can create a virtual computer, enabling you to run a separate operating system within your existing OS. In this example, the host PC is running Windows Vista .
To get started you will need to download the latest version of VirtualBox
Click “next” once you have read the introduction text:
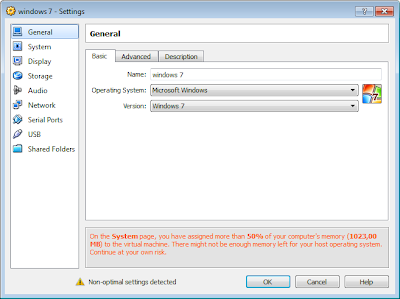
You can now enter a name for your Virtual installation. In this example we have chosen “Windows 7” and selected the “Windows 7” version, as the current version of VirtualBox does not list W7. Once you have done this, click “next”:

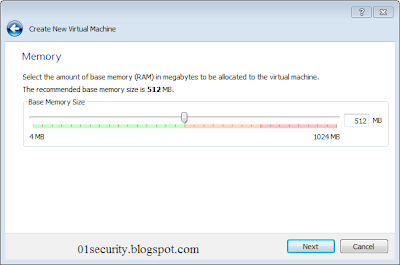
Now choose the amount of RAM you wish to dedicate to the virtual PC.512MB is the minimum, and a sensible value to start with (if you have plenty of memory, you could try 1024MB). Then click “next”:
A virtual hard disk file is needed to store the OS. Click “new” to create a dynamically expanding storage file in a location of your choice. 20GB is a sensible value for a test operating system, assuming you have plenty of spare drive space. Once you have returned to the completed VHD menu, click “next”:

The initial setup is now complete, click “finish” to complete the installation. The main VirtualBox menu will then be displayed, where you can launch the virtual PC or change settings. To configure the Windows 7 VPC, slick “settings”:
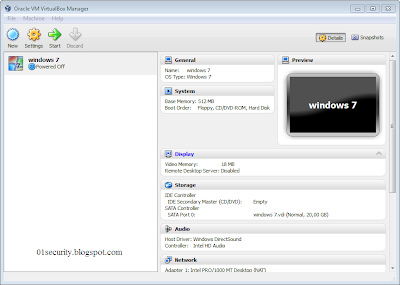
To get the most out of the Windows 7 virtual PC the following configuration changes are recommended:
Then, click CD/DVD-ROM to mount your Windows 7 installation CD (or ISO in this example):

Once these changes have been made, click “ok” to return to the main screen. Then, click “start” (or double click the Windows 7 icon). This will boot the virtual PC and automatically load the Windows 7 setup menu if you have correctly mounted the installation DVD:
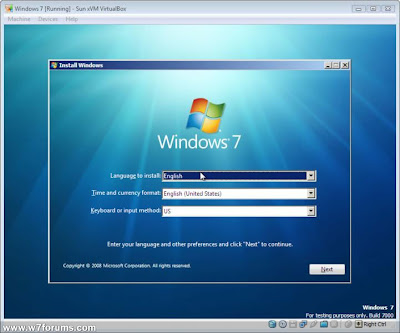
You can then proceed to install Windows 7 as if it was a real PC, safe in the knowledge that it is all done in a virtual environment that won’t interfere with your normal boot OS. If you are an advanced user and wish to install the Guest Additions package, make sure you do this in Vista Compatibility mode for it to work

VirtualBox is an open-source tool from which you can create a virtual computer, enabling you to run a separate operating system within your existing OS. In this example, the host PC is running Windows Vista .
To get started you will need to download the latest version of VirtualBox

Click “next” once you have read the introduction text:

You can now enter a name for your Virtual installation. In this example we have chosen “Windows 7” and selected the “Windows 7” version, as the current version of VirtualBox does not list W7. Once you have done this, click “next”:

Now choose the amount of RAM you wish to dedicate to the virtual PC.512MB is the minimum, and a sensible value to start with (if you have plenty of memory, you could try 1024MB). Then click “next”:

A virtual hard disk file is needed to store the OS. Click “new” to create a dynamically expanding storage file in a location of your choice. 20GB is a sensible value for a test operating system, assuming you have plenty of spare drive space. Once you have returned to the completed VHD menu, click “next”:

The initial setup is now complete, click “finish” to complete the installation. The main VirtualBox menu will then be displayed, where you can launch the virtual PC or change settings. To configure the Windows 7 VPC, slick “settings”:

To get the most out of the Windows 7 virtual PC the following configuration changes are recommended:

- Increase the Video Memory to 64MB and enable 3D acceleration
- Enable audio, and change driver to “Windows Direct Sound”
- Change network adapter to “Intel PRO/1000 MT Desktop”
Then, click CD/DVD-ROM to mount your Windows 7 installation CD (or ISO in this example):

Once these changes have been made, click “ok” to return to the main screen. Then, click “start” (or double click the Windows 7 icon). This will boot the virtual PC and automatically load the Windows 7 setup menu if you have correctly mounted the installation DVD:

You can then proceed to install Windows 7 as if it was a real PC, safe in the knowledge that it is all done in a virtual environment that won’t interfere with your normal boot OS. If you are an advanced user and wish to install the Guest Additions package, make sure you do this in Vista Compatibility mode for it to work
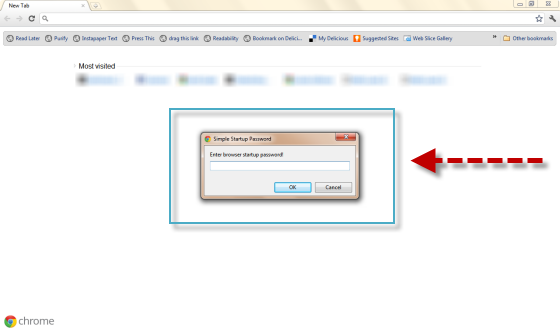
How To:Password Protect your Google Chrome Browser
Password Protect your Chrome Browser to protect you personal browsing data. Chrome saves and keeps a record of your browsing data.
It stores saved passwords, browsing history, download history, cache, autofill form data. And this data could be easily accessed by anyone who uses your computer.
So its very important to protect this info from unauthorized access. ‘Simple Startup Password’ Chrome Extension lets you password protect your chrome browser by adding a functionality to ask for a password before opening and using Chrome browser.
Password Protected Google Chrome
Step 2: Install the extension by clicking Install button
Step 3: After the installation click wrench icon at the top right corner and goto Tools -> Extensions.
Step 4: Search for Simple Startup Password extension and click on Options
Step 5: Enter the login password.
Step 6: That’s it! You’re done.
Now close and open the chrome browser again. You will now be prompted to enter the login password. And you will only be allowed to enter the browser on providing the correct password.
Permutation Iterative : Java : BlueJ
Permutation Iterative : Java : BlueJ
Objective :
BlueJ Program Screenshot :
Java Program Source Code :
The class PermutationIterative computes all the Unique Permutations of a string removing duplicates characters and white spaces. The Algorithm is a simple one ! All the permutations are printed in lexicographic form.
Here the Original string is validated (duplicate and white spaces are removed) and sorted using bubble sort technique. It finds the next Permutation of a given string by the following set of rules:
- Start scanning the string from the end such that arr[i] < arr[i+1]. Here it is advisable to start counting from S.length-1.
- If i occurs to be less than 0, no more permutations are possible.
- Start scanning from end such that arr[j]>arr[i].
- Swap the elements arr[i] and arr[j]
- reverse the elements after arr[i].
- Now you have the next permutation and run a loop until the function return false.
BlueJ Program Screenshot :
Java Program Source Code :
/**
* The class PermutationIterative computes all the Unique Permutations
* of a string removing duplicates characters and whitespaces.
* @AUTHOR SHANTANU KHAN
* @DATE
*/
import java.util.*;
public class PermutationIterative
{
private char[] S; // INSTANCE VARIABLE
private int count;
public PermutationIterative(String Word){ // CONSTRUCTOR
S=removeInvalid(Word).toCharArray();
bubbleSort();
}
private boolean permuteNext()
{
int i,j;
i=S.length-2; // 1. STARTING FROM END FINDING i SUCH THAT S[i]<S[i+1]
while(i>=0 && S[i]>S[i+1])
i--;
if(i<0) // NO MORE PERMUTATIONS POSSIBLE
return false;
j=S.length-1; // 2. ITERATING BACK FINDING j S[j]>S[i]
while((int)S[j]<(int)S[i])
j--;
char temp=S[i]; // 3. SWAPPING arr[i] AND arr[j]
S[i]=S[j];
S[j]=temp;
int f=i+1,b=S.length-1; // 4. REVERSING ELEMENTS AFTER i
while(f<b){
temp=S[f];
S[f++]=S[b];
S[b--]=temp;
}
return true;
}
public void permute(){
System.out.println(S); // PRINT THE ORIGINAL WORD
count++; // FOR THE FIRST PERMUTATION
while(permuteNext()){ // EXECUTION ENDS WITHIN THE permuteNext()
System.out.println(S);
count++;
}
System.out.println("\nNo. of Permutations : "+count);
}
private static String removeInvalid(String s){
String output="";
for(int i=0;i<s.length();i++){
if(!Character.isWhitespace(s.charAt(i))&&(output==""||output.indexOf(s.charAt(i))<0))
output+=s.charAt(i);
}
return output;
}
public void bubbleSort()
{
for(int i=S.length-1;i>0;i--){ // NUMBER OF PASSES
for(int j=0;j<i;j++){ // NUMBER OF COMPARISONS IN EACH PASS
if(S[j]>S[j+1]){ // IF GREATER, SWAPPING J AND J+1 ELEMENT
char temp=S[j]; S[j]=S[j+1]; S[j+1]=temp; // SWAPPING ELEMENTS
}
} // END OF COMPARISION (j) LOOP
} // END OF PASS (i) LOOP
}
public static void main(String[] args){
Scanner sc=new Scanner(System.in);
System.out.print("Enter the Word : ");
PermutationIterative obj=new PermutationIterative(sc.nextLine());
obj.permute();
Tower Of Hanoi Iterative : Java : BlueJ
Objective :
The Tower of Hanoi (also called the Tower of Brahma or Lucas' Tower, and sometimes pluralised) is a mathematical game or puzzle. It consists of three rods, and a number of disks of different sizes which can slide onto any rod. The puzzle starts with the disks in a neat stack in ascending order of size on one rod, the smallest at the top, thus making a conical shape.
BlueJ Program Screenshot :
Java Program Source Code :
The Tower of Hanoi (also called the Tower of Brahma or Lucas' Tower, and sometimes pluralised) is a mathematical game or puzzle. It consists of three rods, and a number of disks of different sizes which can slide onto any rod. The puzzle starts with the disks in a neat stack in ascending order of size on one rod, the smallest at the top, thus making a conical shape.
- Only one disk may be moved at a time.
- Each move consists of taking the upper disk from one of the rods and sliding it onto another rod, on top of the other disks that may already be present on that rod.
- No disk may be placed on top of a smaller disk.
The objective of the puzzle is to move the entire stack to another rod, obeying the following rules:
With three disks, the puzzle can be solved in seven moves.
BlueJ Program Screenshot :
Java Program Source Code :
/**
* The class TowerOfHanoiIterative computes smallest number
* of moves using iteration and without any stack.
* @author SHANTANU KHAN
* @version 1.0.0
*/
import java.util.*;
public class TowerOfHanoiIterative
{
private int nDisks; // INSTANCE VARIABLE
public TowerOfHanoiIterative(int nDisks){ // CONSTRUCTOR
this.nDisks=nDisks;
}
public void execute(){
int n=nDisks; // NUMBER OF DISKS
int limit = (int)Math.pow(2,n)-1; // NUMBER OF ITERATIONS = 2^n - 1
for(int i=0;i<limit;i++){
int disk = disk(i); // DISK TO BE MOVED
int source = ( movements(i,disk)*direction(disk,n))%3; // SOURCE PEG
int destination = (source + direction(disk,n))%3; // DESTINATION PEG
move(disk,source,destination);
}
}
private int disk(int i) { // RETURNS THE DISK TO BE MOVED IN i
int C, x= i+1; // SINCE FOR STARTS WITH 0, ADDING 1
for(C=0;x%2==0;C++){ // CONTINUOUS DIVISION BY 2 UNTIL ODD OCCURS
x/=2;
}
return C; // RETURNS THE COUNTER C
}
private int movements(int i, int d) { // HOW MANY TIMES DISK d HAS MOVED BEFORE STAGE i
while(d--!=0)
i/=2;
return (i+1)/2;
}
private int direction(int d,int n) { // EACH DISK MOVES IN SAME DIRECTION CW=1, ACW=2
return 2 - (n + d)%2;
}
private void move(int disk, int source, int destination) {
System.out.println("Move Disk " + (disk+1)+ " from Tower " + (source+1) + " to Tower " + (destination+1));
}
public static void main(String[] args){
Scanner sc=new Scanner(System.in);
System.out.print("Enter the No. of Disks : ");
TowerOfHanoiIterative toh=new TowerOfHanoiIterative(sc.nextInt());
toh.execute();
}
}
System Utility : TAIL : Java
Objective :
BlueJ Program Screenshot :
Java Program Source Code :
Syntax: tail [-n] filename.extThis Program will print the last n lines of the Specified file. If the switch n is omitted, it will show the last 10 lines. If the file contains less, It Shows the Full Content. The Program here has been done by first reading the number of lines and then skipping lines which are not to be printed. The other way around would be to use a circular link list of size n but this process is faster as it doesn't stores the lines extracted by the file reader object.
BlueJ Program Screenshot :
Java Program Source Code :
/**
* < Syntax: [-h] filename.ext > will print the last n lines of the Specified file.
* If the switch n is omitted, it will show the last 10 lines. If the file contains less,
* It Shows the Full Content.
* Author SHANTANU KHAN
* Date 26/06/2012
*/
import java.io.*;
public class tail
{
// INSTANCE VARIABLES
private int lines,present; // FILE SIZE AND EXISTING NO. OF LINES
private String file; // FILE NAME OR LOCATION TO BE READ
public tail(String file){ // CONSTRUCTOR
this.file=file;
present=countLines(file); // COUNTS THE NO. OF LINES PRESENT IN THE FILE.
lines=10; // DEFAULT NO. OF LINES
}
public tail(String file,int printLines){ // CONSTRUCTOR
this.file=file;
present=countLines(file);
lines=printLines;
}
public static int countLines(String file){ // COUNT AND RETURN THE NUMBER OF LINES
try{
BufferedReader rFile=new BufferedReader(new FileReader(file));
int count=0; String s;
while(rFile.readLine()!=null) // READING THE FILE LINE-WISE
count++; // INCREMENTING COUNTER
rFile.close(); return count;
}
catch(Exception E){
System.out.println("\nFile Not Found or UnReadAble.\n"+E);
System.exit(-1); return -1; // RETURN STATEMENT NECESSARY
}
}
private void printLine(){ // PRINT THE DATA IN THE SPECIFIED FILE
int skip=0; // DEFAULT IF LINES >=AVAILABLE, SKIPS NOTHING
if(lines<0){ // IF PARAMETER WITH SWITCH HAS NEGATIVE NUMBER : --23 TEST.TXT
System.out.println("Error : Parameter Was Below Minimum Limit Of 0.");
System.exit(-1); } // EXITS IF n NEGATIVE
else if(lines<present)
skip=present-lines; // WILL SKIP PRINTING OF THE LINES
try{ // EXCEPTION MAY BE THROWN IN RARE CASES, ALREADY FILE CHECKED DURING COUNT LINES
BufferedReader rFile=new BufferedReader(new FileReader(file));
String s;
while(skip-->0) // READING THE FILE LINE-WISE
s=rFile.readLine();
while((s=rFile.readLine())!=null) // READING THE FILE LINE-WISE
System.out.println(s);
rFile.close();
}
catch(Exception E){;}
}
public static void main(String[] args){
if(args.length==0){
System.out.println("\nSyntax : tail [-n] fileName.ext\nn = Number of Lines to Print.");
System.exit(-1); // STOP EXECUTION
}
if(args.length==1){ // 1 PARAMETER PROVIDED
if(args[0].charAt(0)=='-'){ // ONLY SWITCH PROVIDED AS INPUT
System.out.println("\nFileName Missing in Parameter.\nSyntax : tail [-n] fileName.ext\nn = Number of Lines to Print.");
System.exit(-1); // STOP EXECUTION
}
else{ // ONLY FILENAME PROVIDED IN PARAMETER
System.out.println("\nFile Accessed : "+args[0]+"\n");
tail obj=new tail(args[0]);
obj.printLine();
}
}
else if(args.length>=2){
if(args.length>2)
System.out.println("\nExcess Parameters Will Be Ignored.");
if(args[0].charAt(0)=='-'){
int n=Integer.parseInt(args[0].substring(1));
System.out.println("\nFile Accessed : "+args[1]+"\n");
tail obj=new tail(args[1],n);
obj.printLine();
}
else{
System.out.println("\nFile Accessed : "+args[0]+"\n");
tail obj=new tail(args[0]);
obj.printLine();
7 Segment Display : Java : BlueJ
Objective :
A seven-segment display (SSD), or seven-segment indicator, is a form of electronic display device for displaying decimal numerals that is an alternative to the more complex dot-matrix displays. Seven-segment displays are widely used in digital clocks, electronic meters, and other electronic devices for displaying numerical information. A seven segment display, as its name indicates, is composed of seven elements. Individually on or off, they can be combined to produce simplified representations of the arabic numerals. Often the seven segments are arranged in an oblique (slanted) arrangement, which aids readability. In most applications, the seven segments are of nearly uniform shape and size (usually elongated hexagons, though trapezoids and rectangles can also be used), though in the case of adding machines, the vertical segments are longer and more oddly shaped at the ends in an effort to further enhance readability.
Each of the numbers 0, 6, 7 and 9 may be represented by two or more different glyphs on seven-segment displays.
The seven segments are arranged as a rectangle of two vertical segments on each side with one horizontal segment on the top, middle, and bottom. Additionally, the seventh segment bisects the rectangle horizontally. There are also fourteen-segment displays and sixteen-segment displays (for full alphanumerics); however, these have mostly been replaced by dot-matrix displays.
The segments of a 7-segment display are referred to by the letters A to G, as shown to the right, where the optional DP decimal point (an "eighth segment") is used for the display of non-integer numbers.
BlueJ Program Screenshot :
Java Program Source Code :
The Source Code Uses Certain Image Files So : For Proper Distribution, The Program is Available for Download in Two Formats :
1. For Windows (Direct Executable .exe) Recommended [Link] : http://www.fileden.com/files/2012/1/12/3250168/7SegmentDigitalBCD.zip
2. For Other Platform (Mac, Ubuntu, Linux) [Link] :
http://www.fileden.com/files/2012/1/12/3250168/DigitalBCD.jar
 |
| 7 Segment Display with 0-F with Decimal Point |
 |
| Truth Table Of A Seven Segmented Display 0-9 |
The seven segments are arranged as a rectangle of two vertical segments on each side with one horizontal segment on the top, middle, and bottom. Additionally, the seventh segment bisects the rectangle horizontally. There are also fourteen-segment displays and sixteen-segment displays (for full alphanumerics); however, these have mostly been replaced by dot-matrix displays.
The segments of a 7-segment display are referred to by the letters A to G, as shown to the right, where the optional DP decimal point (an "eighth segment") is used for the display of non-integer numbers.
BlueJ Program Screenshot :
Java Program Source Code :
The Source Code Uses Certain Image Files So : For Proper Distribution, The Program is Available for Download in Two Formats :
1. For Windows (Direct Executable .exe) Recommended [Link] : http://www.fileden.com/files/2012/1/12/3250168/7SegmentDigitalBCD.zip
2. For Other Platform (Mac, Ubuntu, Linux) [Link] :
http://www.fileden.com/files/2012/1/12/3250168/DigitalBCD.jar
Open URL In Default System Browser : Java : BlueJ
Objective :
Opening an URL from your Java Program in the User-Default browser, with Java SE 6 there is. Unless your platform doesn't support this. Well Most Platform Running Latest Version of Java and With A Default Browser Would Do It Fine !
In Java SE 6 a new class has been added to the java.awt package: Desktop. This class has a public class method isDesktopSupported() which returns true if the class is supported on the current platform, and false otherwise.
If the class is supported, you can retrieve an instance using the class method getDesktop().
You can use the browse() method to display a URI in the default browser. If this browser is not able to handle the specified URI, the application registered for handling the URIs of the specified type is invoked. For example, the URI news:comp.lang.perl.misc might invoke a Usenet client.
However, before you call the browse() method make sure to check if this action is supported on the current platform by calling the isSupported() method with java.awt.Desktop.Action.BROWSE as the value of the first and only parameter.
Note that even though this method returns true, it's still possible that the platform doesn't support the URI - for example if there is no application registered for the given scheme. In this case the browse() method will throw an IOException.
Besides the browse() method there are 5 more methods, providing support for the 4 following Desktop actions:
EDIT : The edit() method launches the associated editor application and opens a file for editing.
MAIL : There are two mail() methods. The first one doesn't take any parameters and launches the mail composing window of the user-default mail client. The second method takes a single parameter: a "mailto" URI. : It also launces the mail composing window of the user-default mail client, but additionally fills in the message fields specified by the "mailto" URI (for example, to, subject, etc.).
OPEN : The open() method launches the associated application to open the file. If the specified file is a directory, the file manager of the current platform is launched to open it.
PRINT : Prints a file with the native desktop printing facility, using the associated application's print command.
BlueJ Program Screenshot :
Java Program Source Code :
Opening an URL from your Java Program in the User-Default browser, with Java SE 6 there is. Unless your platform doesn't support this. Well Most Platform Running Latest Version of Java and With A Default Browser Would Do It Fine !
In Java SE 6 a new class has been added to the java.awt package: Desktop. This class has a public class method isDesktopSupported() which returns true if the class is supported on the current platform, and false otherwise.
If the class is supported, you can retrieve an instance using the class method getDesktop().
You can use the browse() method to display a URI in the default browser. If this browser is not able to handle the specified URI, the application registered for handling the URIs of the specified type is invoked. For example, the URI news:comp.lang.perl.misc might invoke a Usenet client.
However, before you call the browse() method make sure to check if this action is supported on the current platform by calling the isSupported() method with java.awt.Desktop.Action.BROWSE as the value of the first and only parameter.
Note that even though this method returns true, it's still possible that the platform doesn't support the URI - for example if there is no application registered for the given scheme. In this case the browse() method will throw an IOException.
Besides the browse() method there are 5 more methods, providing support for the 4 following Desktop actions:
EDIT : The edit() method launches the associated editor application and opens a file for editing.
MAIL : There are two mail() methods. The first one doesn't take any parameters and launches the mail composing window of the user-default mail client. The second method takes a single parameter: a "mailto" URI. : It also launces the mail composing window of the user-default mail client, but additionally fills in the message fields specified by the "mailto" URI (for example, to, subject, etc.).
OPEN : The open() method launches the associated application to open the file. If the specified file is a directory, the file manager of the current platform is launched to open it.
PRINT : Prints a file with the native desktop printing facility, using the associated application's print command.
BlueJ Program Screenshot :
Java Program Source Code :
/**
* The Program Runs in Command Prompt Or in IDE using URLs
* in the form of Parameters. All URLs must be in http:// form.
* © SHANTANU KHAN
* @ shantanukhan1995@gmail.com
* @website 0code.blogspot.com
* Program Type : BlueJ Program - Java
*/
import java.net.URI;
import java.awt.Desktop;
public class OpenURL
{
public static void main(String[] args)
{
if(!java.awt.Desktop.isDesktopSupported())
{
System.err.println("Desktop is not supported (fatal)");
System.exit(1);
}
if(args.length==0)
{
System.out.println( "Usage: OpenURI [URI [URI ... ]]" );
System.exit( 0 );
}
java.awt.Desktop desktop = java.awt.Desktop.getDesktop();
if(!desktop.isSupported(java.awt.Desktop.Action.BROWSE))
{
System.err.println( "Desktop doesn't support the browse action (fatal)" );
System.exit( 1 );
}
for(String arg:args)
{
try{
java.net.URI uri = new java.net.URI(arg);
desktop.browse( uri );
}
catch(Exception e){
System.err.println(e.getMessage());
}
}
}
Gauss Matrix Elimination : Java : BlueJ
" I would like to show my Acknowledgement and special Thanks to the Original Author Of Many of the Programs in this Blog : Sir A.K. Seal who has shown great teaching skills to make Programming Practical and Simple. "Objective :
In linear algebra, Gaussian elimination is an algorithm for solving systems of linear equations. It can also be used to find the rank of a matrix, to calculate the determinant of a matrix, and to calculate the inverse of an invertible square matrix. The method is named after Carl Friedrich Gauss, but it was not invented by him.
Elementary row operations are used to reduce a matrix to what is called triangular form (in numerical analysis) or row echelon form (in abstract algebra). Gauss–Jordan elimination, an extension of this algorithm, reduces the matrix further to diagonal form, which is also known as reduced row echelon form. Gaussian elimination alone is sufficient for many applications, and requires fewer calculations than the Gauss–Jordan version.
The process of Gaussian elimination has two parts. The first part (Forward Elimination) reduces a given system to either triangular or echelon form, or results in a degenerate equation, indicating the system has no unique solution but may have multiple solutions. This is accomplished through the use of elementary row operations. The second step uses back substitution to find the solution of the system above.
Stated equivalently for matrices, the first part reduces a matrix to row echelon form using elementary row operations while the second reduces it to reduced row echelon form, or row canonical form.
Another point of view, which turns out to be very useful to analyze the algorithm, is that Gaussian elimination computes a matrix decomposition. The three elementary row operations used in the Gaussian elimination (multiplying rows, switching rows, and adding multiples of rows to other rows) amount to multiplying the original matrix with invertible matrices from the left. The first part of the algorithm computes an LU decomposition, while the second part writes the original matrix as the product of a uniquely determined invertible matrix and a uniquely determined reduced row-echelon matrix.
BlueJ Program Screenshot :Example :
Suppose the goal is to find and describe the solution(s), if any, of the following system of linear equations:
The algorithm is as follows: eliminate x from all equations below  , and then eliminate y from all equations below
, and then eliminate y from all equations below  . This will put the system into triangular form. Then, using back-substitution, each unknown can be solved for.
. This will put the system into triangular form. Then, using back-substitution, each unknown can be solved for.
In the example, x is eliminated from  by adding
by adding  to
to  . x is then eliminated from
. x is then eliminated from  by adding
by adding  to
to  . Formally:
. Formally:
The result is:
Now y is eliminated from  by adding
by adding  to
to  :
:
The result is:
This result is a system of linear equations in triangular form, and so the first part of the algorithm is complete.
The last part, back-substitution, consists of solving for the knowns in reverse order. It can thus be seen that
Then,  can be substituted into
can be substituted into  , which can then be solved to obtain
, which can then be solved to obtain
Next, z and y can be substituted into  , which can be solved to obtain
, which can be solved to obtain
The system is solved.
Some systems cannot be reduced to triangular form, yet still have at least one valid solution: for example, if y had not occurred in  and
and  after the first step above, the algorithm would have been unable to reduce the system to triangular form. However, it would still have reduced the system to echelon form. In this case, the system does not have a unique solution, as it contains at least one free variable. The solution set can then be expressed parametrically (that is, in terms of the free variables, so that if values for the free variables are chosen, a solution will be generated).
after the first step above, the algorithm would have been unable to reduce the system to triangular form. However, it would still have reduced the system to echelon form. In this case, the system does not have a unique solution, as it contains at least one free variable. The solution set can then be expressed parametrically (that is, in terms of the free variables, so that if values for the free variables are chosen, a solution will be generated).
In practice, one does not usually deal with the systems in terms of equations but instead makes use of the augmented matrix (which is also suitable for computer manipulations). For example:
Therefore, the Gaussian Elimination algorithm applied to the augmented matrix begins with:
which, at the end of the first part (Gaussian elimination, zeros only under the leading 1) of the algorithm, looks like this:
That is, it is in row echelon form.
At the end of the algorithm, if the Gauss–Jordan elimination(zeros under and above the leading 1) is applied:
That is, it is in reduced row echelon form, or row canonical form.
Java Program Source Code :
/**
* The Program Takes Number of Eqautions and Then Creates An
* Square Matrix of Order x Order and Formulates a Top Triangle
* My Continuous Elimination and Then Solves the Set of Equations
* to Find the Values of the Order number of Variables.
* @author SHANTANU KHAN
* @mail shantanukhan1995@gmail.com
* @website 0code.blogspot.com
* Program Type : BlueJ Program - Java
*/
import java.util.*;
public class GaussMatrix
{
// INSTANCE VARIABLES
private double[][] m; // MATRIX OF CO-EFFICIENTS
private double[] constants; // VECTOR OF CONSTANT TERMS
private double[] solution; // SOLUTION SET
private int numEq; // NUMBER OF EQUATIONS
static Scanner sc=new Scanner(System.in);
public GaussMatrix(int equations) // CONSTRUCTOR
{
numEq=equations;
m=new double[numEq][numEq];
constants=new double[numEq];
solution=new double[numEq];
}
public void fillMatrix()
{
for(int i=0;i<numEq;i++){
System.out.println("Enter the co-efficients of unknowns and constant term for Equation "+(i+1)+" :");
for(int j=0;j<numEq;j++){
System.out.print("Enter Co-efficient "+(j+1)+" : ");
m[i][j]=sc.nextDouble();
}
System.out.print("Enter Constant Term : ");
constants[i]=sc.nextDouble();
}
}
public void printSolution()
{
System.out.println("\nSolution Set is : ");
for(int i=0;i<numEq;i++)
System.out.println((char)('A'+i)+" = "+solution[i]);
}
public void printMatrix() // FOR DEBUGGING PURPOSE
{
for(int i=0;i<numEq;i++){
for(int j=0;j<numEq;j++){
if(m[i][j]>=0)
System.out.print(" +"+m[i][j]+((char)('A'+j))+" ");
else if(m[i][j]<0)
System.out.print(" "+m[i][j]+((char)('A'+j))+" ");
}
System.out.println(" = "+constants[i]);
}
}
public void swapRows(int row1,int row2)
{
double temp;
for(int j=0;j<numEq;j++){ // SWAPPING CO-EFFICIENT ROWS
temp=m[row1][j];
m[row1][j]=m[row2][j];
m[row2][j]=temp;
}
temp=constants[row1]; // SWAPPING CONSTANTS VECTOR
constants[row1]=constants[row2];
constants[row2]=temp;
}
public void eliminate()
{
int i,j,k,l;
for(i=0;i<numEq;i++){ // i -> ROW ; MATRIX ORDER DECREASES DURING ELIMINATION
// FIND LARGEST CO-EFFICIENTSOF THE CURRENT COLUMN MOVING ROW-WISE
double largest=Math.abs(m[i][i]);
int index=i;
for(j=i+1;j<numEq;j++){
if(Math.abs(m[j][i])>largest){
largest=m[j][i];
index=j;
}
}
swapRows(i,index); // SWAPPING i-th ROW to index-th ROW
for(k=i+1;k<numEq;k++){
double factor=m[k][i]/m[i][i];
// PROCESSING COLUMN WISE
for(l=i;l<numEq;l++){
m[k][l]-=factor*m[i][l];
}
constants[k]-=factor*constants[i]; // PROCESSING CONSTANTS
}
}
}
public void solve()
{
for(int i=numEq-1;i>=0;i--){
solution[i]=constants[i]; // COPY
for(int j=numEq-1;j>i;j--){
solution[i]-=m[i][j]*solution[j];
}
solution[i]/=m[i][i];
}
}
public static void main(String args[])
{
System.out.print("Enter the Number of Terms : ");
GaussMatrix obj=new GaussMatrix(sc.nextInt());
obj.fillMatrix();
System.out.println("\fYou Have Entered The Following Equations :");
obj.printMatrix();
obj.eliminate();
obj.solve();
obj.printSolution();
Subscribe to:
Posts (Atom)